With the recent Azure Security Center updates from September, it now has the ability to help prevent misconfigurations of new resources with regard to specific recommendations. This feature can help keep your workloads secure and stabilize your secure score.
Enforcing a secure configuration, based on a specific recommendation, is offered in two modes:
- Deny
- Enforce
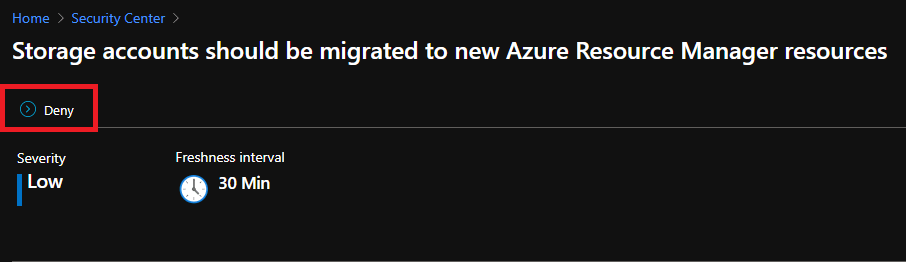
The option to configure a deny effect or enforce remediation of non-compliant resources can be found at the top of the recommendation details page.
Deny
Using the Deny effect of Azure Policy, you can stop unhealthy resources from being created
These recommendations can be used with the deny option:
- Virtual machines should be migrated to new Azure Resource Manager resources
- Storage accounts should be migrated to new Azure Resource Manager resources
- All authorization rules except RootManageSharedAccessKey should be removed from Event Hub namespace
- All authorization rules except RootManageSharedAccessKey should be removed from Service Bus namespace
- Secure transfer to storage accounts should be enabled
- Only secure connections to your Redis Cache should be enabled
- Automation account variables should be encrypted
- Service Fabric clusters should only use Azure Active Directory for client authentication
- Service Fabric clusters should have the ClusterProtectionLevel property set to EncryptAndSign
- Audit unrestricted network access to storage accounts
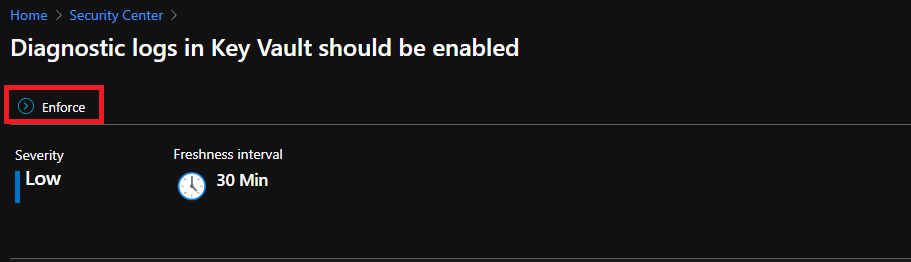
Enforce
Using the Enforce option, you can take advantage of Azure policy’s DeployIfNotExist effect and automatically remediate non-compliant resources upon creation
These recommendations can be used with the enforce option:
- Diagnostic logs in Logic Apps should be enabled
- Diagnostic logs in Data Lake Analytics should be enabled
- Diagnostic logs in IoT Hub should be enabled
- Diagnostic logs in Batch accounts should be enabled
- Diagnostic logs in Azure Stream Analytics should be enabled
- Diagnostic logs in Service Bus should be enabled
- Diagnostic logs in Search services should be enabled
- Diagnostic logs in Event Hub should be enabled
- Diagnostic logs in Virtual Machine Scale Sets should be enabled
- Diagnostic logs in Key Vault should be enabled
- Auditing on SQL server should be enabled
- Advanced data security should be enabled on your SQL servers
For more information about preventing misconfigurations using Azure Security Center see the following documentation:
https://docs.microsoft.com/en-us/azure/security-center/prevent-misconfigurations
The Azure Security Center September 2020 release notes:
https://docs.microsoft.com/en-us/azure/security-center/release-notes?s=09#september-2020