Key Vault access policies allow you to set very specifically what rights an identity has on keys, secrets, and certificates. However, you have to set this per key vault, and you cannot use the resource hierarchy within Azure (e.g. Management Groups, Subscriptions, and Resource Groups).
Azure role-based access control (Azure RBAC) is built on top of Azure Resource Manager (ARM) and already allows a variety of resources to leverage built-in roles, which allow you to assign the set of permissions (that a role basically is) to an identity (user, group, service principal, or managed identity) on different scope levels: management group, subscription, resource group, or individual resources.
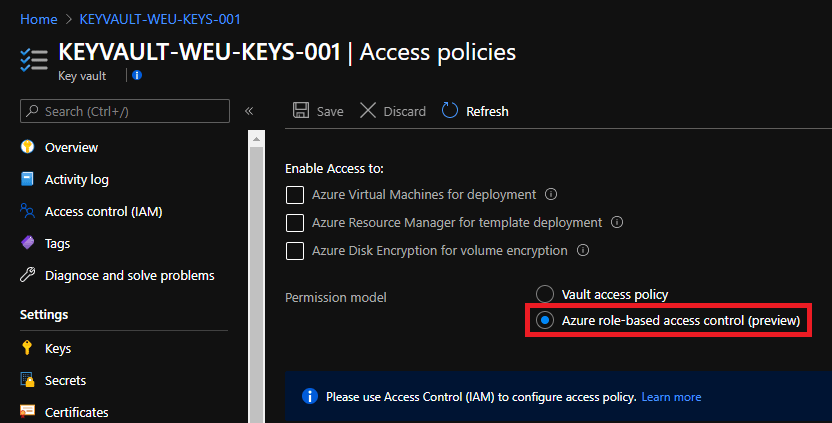
Fortunately, it has recently become possible to use the Azure RBAC model within Key Vault. For this, you have to refrain from using the well-known access policies, but you can start quickly because a number of predefined roles (see list below) are already available. You can assign these roles at all scope levels, including individual keys, secrets, and certificates. It provides you one place to manage all permissions across all your Key Vaults.
Note: While the Key Vault resource provider can handle both vaults and managed Hardware Security Modules (HSM), Azure RBAC does only support vaults as of this moment.
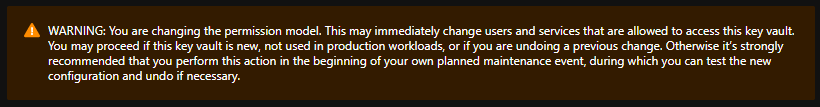
Note 2: When the Key Vault permission model is changed to use Azure RBAC, the existing access policies are no longer valid. Before making the change, make sure that the correct Azure RBAC roles are assigned to prevent any issues.
Below is an overview of the full list of new built-in roles that apply to Azure Key Vault. To view the exact permissions assignments per role, follow the link of the role.
| Built-in role | Description | ID |
|---|---|---|
| Key Vault Administrator (preview) | Perform all data plane operations on a key vault and all objects in it, including certificates, keys, and secrets. Cannot manage key vault resources or manage role assignments. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | 00482a5a-887f-4fb3-b363-3b7fe8e74483 |
| Key Vault Certificates Officer (preview) | Perform any action on the certificates of a key vault, except manage permissions. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | a4417e6f-fecd-4de8-b567-7b0420556985 |
| Key Vault Crypto Officer (preview) | Perform any action on the keys of a key vault, except manage permissions. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | 14b46e9e-c2b7-41b4-b07b-48a6ebf60603 |
| Key Vault Crypto Service Encryption (preview) | Read metadata of keys and perform wrap/unwrap operations. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | e147488a-f6f5-4113-8e2d-b22465e65bf6 |
| Key Vault Crypto User (preview) | Perform cryptographic operations using keys. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | 12338af0-0e69-4776-bea7-57ae8d297424 |
| Key Vault Reader (preview) | Read metadata of key vaults and its certificates, keys, and secrets. Cannot read sensitive values such as secret contents or key material. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | 21090545-7ca7-4776-b22c-e363652d74d2 |
| Key Vault Secrets Officer (preview) | Perform any action on the secrets of a key vault, except manage permissions. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | b86a8fe4-44ce-4948-aee5-eccb2c155cd7 |
| Key Vault Secrets User (preview) | Read secret contents. Only works for key vaults that use the ‘Azure role-based access control’ permission model. | 4633458b-17de-408a-b874-0445c86b69e6 |
For more information about Azure role-based access control in combination with Key vault see the following documentation: https://docs.microsoft.com/en-us/azure/key-vault/general/rbac-guide